To use single sign on, your client calls the LoginByToken method. Your client must send a SAML token to the vCenter Server by embedding the token in the SOAP header for the LoginByToken request. During the login sequence, your client must save and restore the HTTP session cookie. The vCenter Single Sign-On SDK contains sample code that demonstrates how to use the LoginByToken method.
The following sections describe examples of using the LoginByToken method to establish a vCenter Single Sign On session with a vCenter Server.
The following sections describe a C# example of using the LoginByToken method.
After you obtain a SAML token from the vCenter Single Sign On Server, you can use the vSphere API method LoginByToken to establish a single sign on session with a vCenter Server. To establish a vCenter Server session that is based on SAML token authentication, the client must embed the SAML token in the SOAP header of the LoginByToken request. The C# LoginByToken example uses the following .NET services to support a single sign on session.
|
The sample creates a custom policy assertion derived from the SecurityPolicyAssertion class. The custom assertion contains the SAML token and X509 certificate.
|
|
|
The sample defines a custom output filter derived from the SendSecurityFilter class. The custom filter adds the token and certificate to the outgoing SOAP message.
|
|
|
The sample uses the ServicePointManager to specify SSL3 and HTTP 100-Continue behavior.
|
|
|
The sample uses the ConfigurationManager to specify certificate metadata (password and certificate type).
|
|
|
The sample uses the CookieContainer class to manage vCenter session cookies.
|
The LoginByToken request includes the SAML token and client certificate security assertions for client authentication. After successful login, the authentication overhead is no longer needed. The client resets the VimService context to eliminate the security overhead. Subsequent client requests will contain the session cookie, which is enough to support the persistent, authenticated session.
The code examples in the following sections show how to use the LoginByToken method with a holder-of-key security token. The code examples are based on the LoginByTokenSample project contained in the vCenter Single Sign On SDK. The project is located in the dotnet samples directory (SDK/ssoclient/dotnet/cs/samples/LoginByToken).
|
■
|
Project file – LoginByToken.csproj
|
|
■
|
Sample code – LoginByTokenSample.cs
|
|
■
|
SOAP header manipulation code – CustomSecurityAssertionHok.cs
|
The LoginByTokenSample class constructor creates the following elements to set up access to the vCenter Server.
|
■
|
VimService object – Provides access to vSphere API methods and support for security policies and session cookie management. It also stores the vCenter Server URL.
|
|
■
|
CookieContainer – Provides local storage for the vCenter Server session cookie.
|
|
■
|
ManagedObjectReference – Manually created ManagedObjectReference to retrieve a ServiceInstance at the beginning of the session.
|
The following code fragment shows the LoginByTokenSample constructor.
Example: LoginByTokenSample Constructor
The client must obtain a SAML token from a vCenter Single Sign-On Server. See the vCenter Single Sign-On Programming Guide.
The LoginByToken sample creates a custom policy assertion that is derived from the .NET class SecurityPolicyAssertion. The assertion class gives the .NET framework access to the SAML token and the X509 certificate.
|
■
|
Sets the ServicePointManager properties to specify SSL3 and HTTP 100-Continue response handling. 100-Continue response handling supports more efficient communication between the client and vCenter Server. When the client-side .NET framework sends a request to the Server, it sends the request header and waits for a 100-Continue response from the Server. After it receives that response, it sends the request body to the Server.
|
|
■
|
Creates an X509Certificate2 object, specifies the certificate file, and imports the certificate. The certificate file specification indicates a PKCS #12 format file (Public-Key Cryptography Standards) – PfxCertificateFile. The file contains the client’s private key and public certificate. The PfxCertificateFile setting is defined in the app.config file in the LoginByToken project. The definition specifies the location of the file.
|
|
■
|
|
■
|
Defines a custom output filter that is derived from the .NET class SendSecurityFilter.
|
The following code fragment shows the LoginByTokenSample class method GetSecurityPolicyAssertionForHokToken. The method returns a CustomSecurityAssertionHok instance which overrides the .NET class SecurityPolicyAssertion. The security assertion contains the SAML token and the X509 certificate token. This code is taken from the LoginByToken project file samples/LoginByToken/CustomSecurityAssertionHok.cs.
Example: Setting Up Security Policies
|
■
|
SecureMessage – An override method for the .NET method SendSecurityFilter.SecureMessage. The override method adds the SAML token and message signature to the .NET Security element.
|
|
■
|
|
■
|
Calls the LoginByTokenSample class method GetSecurityPolicyAssertionForHokToken (see Security Policies) and adds the security policy to the VimService object.
|
The VimService object contains the following data:
|
■
|
Calls the RetrieveServiceContent method. The method establishes the connection with the vCenter Server and provides access to the SessionManager managed object.
|
|
■
|
Calls the LoginByToken method. The .NET framework uses the security policy assertion to construct the login request. The response includes a session cookie.
|
|
■
|
Calls the LoginByTokenSample class method resetService to create a new VimService object. The session cookie is stored in the cookie container in the VimService object.
|
Example: Connection and Login
The following code fragment shows the resetService method. The method creates a new VimService object and a new cookie container. The method also adds the session cookie to the cookie container.
Example: The resetService method
The following example is based on the LoginByTokenSample.java file contained in the vCenter Single Sign On SDK. The SDK contains Java code that supports HTTP and SOAP header manipulation.
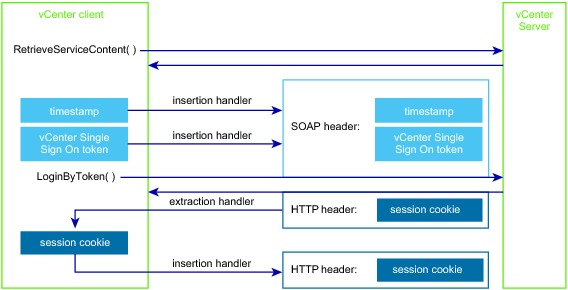
After you obtain a SAML token from the vCenter Single Sign-On Server, you can use the vSphere Web Services API method LoginByToken to establish a vCenter Single Sign-On session with a vCenter Server. At the beginning of the session, your client is responsible for the following tasks:
|
■
|
Insert the vCenter Single Sign-On token and a timestamp into the SOAP header of the LoginByToken message.
|
|
■
|
If at a later time your client invokes the LoginByToken method, or other login method, the Server issues a new session cookie in response. You must have a cookie handler in place to save the cookie for subsequent requests.
|
|
1
|
Call the RetrieveServiceContent method to establish an HTTP connection with the vCenter Server and save the HTTP session cookie.
|
|
2
|
Call the LoginByToken method to authenticate the vCenter session. To send the token to the vCenter Server, the client uses a handler to embed the token and a time stamp in the SOAP header for the message. The client uses an HTTP header handler method to extract the cookie from the vCenter Server response.
|
|
3
|
Restore the session cookie for future requests. To identify the session started with the LoginByToken method, the client uses a handler to embed the session cookie in the HTTP header.
|
|
■
|
An extraction handler obtains the HTTP session cookie provided by the vCenter Server. After setting up the handler, a call to the LoginByToken method will invoke the handler to extract the cookie from the Server response.
|
|
The example code also uses multiple calls to the VimPortType.getVimPort method to manage the request context. The getVimPort method clears the HTTP request context. After each call to the getVimPort method, the client resets the request context endpoint address to the vCenter Server URL. After the client has obtained the session cookie, it will restore the cookie in subsequent requests.
|
The code examples in the following sections show how to use the LoginByToken method with a holder-of-key security token. The code examples are based on the sample code contained in the vCenter Single Sign On SDK. The files are located in the Java samples directory (SDK/ssoclient/java/JAXWS/samples):
|
■
|
SOAP header handlers. These are the same handlers that are used in the vCenter Single Sign-On example in vCenter Single Sign On Programming Guide. The SOAP handler files are contained in the vCenter Single Sign-On SDK and are located in the SSO client soaphandlers directory:
|
|
|||
|
|||
|
|||
The code fragment in this section sets up the message handlers and calls the LoginByToken method. The following sequence describes the steps and shows the corresponding objects and methods.
|
|||
The following examples shows Java code that calls the LoginByToken method.
Example: Using LoginByToken
|
|||
The following example shows Java code that restores the vCenter session. This code requires the vCenter URL and the cookie and default handler that were retrieved before login. See Sample Code.
Example: Restoring the vCenter Server Session