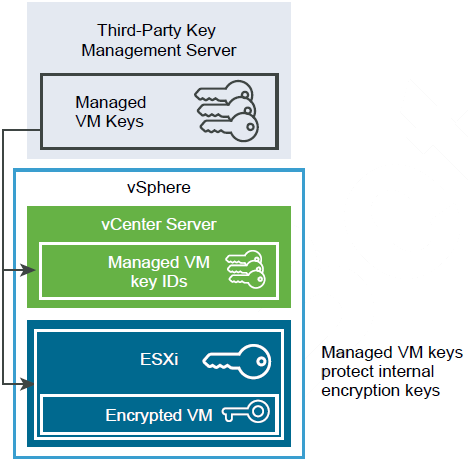
The vCenter Server checks the privileges of users who perform cryptographic operations. You can use the vSphere Web Client to assign cryptographic privileges or to assign the No cryptography administrator custom role to groups of users. See Prerequisites and Required Privileges for Encryption Tasks.
|
■
|
|
■
|