Report Accessible Storage Extents
This example shows how to report the disk storage extents that are accessible to a given SCSI controller. The information can be useful for configuring the managed servers in a datacenter.
This example assumes you have already located an instance of CIM_ComputerSystem subclassed as ACME_Controller that represents the RAID controller. See Monitor RAID Controller State for information about locating the RAID controllers attached to a managed system.
This example is based on the assumption that you have already installed a VIB that contains an implementation of the Host Hardware RAID profile, defined by the SNIA. VMware does not implement this profile, but prominent hardware vendors provide implementations for their storage controllers.
This example is based on the assumption that the implementation on the managed server models serial-attached SCSI connections to drives that belong to pooled RAID configurations. This model is similar to the SMI-S Host Hardware RAID Controller profile published by the SNIA.
The model might or might not correspond to your hardware vendor’s implementation. Contact the hardware vendor for more information about the implementation.
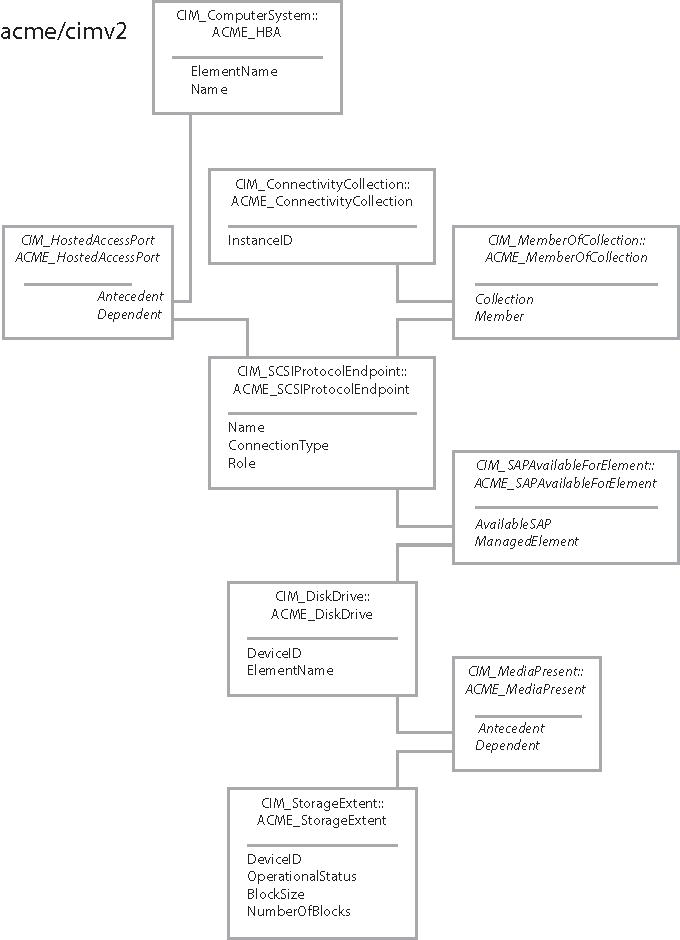
Locating Storage Extents Attached to SCSI Targets shows the relationships of the CIM objects involved. Locating Storage Extents Attached to SCSI Targets uses a fictitious namespace and class names that begin with the prefix ACME_.
The SMI-S specifies two different ways to model connections between targets and initiators. If your hardware vendor’s implementation uses the CIM_SCSIInitiatortargetLogicalUnitPath association, you can follow the LogicalUnit reference of that association to get to the LUN directly.
Another way to locate disk storage extents is to start from each instance of CIM_ConnectivityCollection connected to the controller and to follow a series of associations to the disk media attached to the target endpoint. This procedure begins with the reverse of the last step in Monitor State of RAID Connections, except that you need to filter on the value of the Role property to retrieve only targets, not initiators.
This example bypasses the issue of implementation choice by going from the SCSI controller to the target endpoints in one step by using the CIM_HostedAccessPort association. With this approach, the hardware vendor’s choice of SMI-S implementation does not matter.
This pseudocode depends on the pseudocode in Make a Connection to the CIMOM and Mapping Integer Property Values to Strings.
To report available storage extents